A follow-up to Part 1: 'Does Cybersecurity Solution Architecture Matter?'.
On the Road
By the spring of 2010, I've been living out of my suitcase for the majority of the past four years. Being a part of global professional services for a rapidly growing SIEM vendor meant that my team had barely enough “me time” to do laundry on weekends. One customer lovingly referred to me as "urban hobo."
Why would I put up with this lifestyle for so long? Sure, the pay was reasonable, but the burnout was all too real.
I stuck around because I was enamored with the technology we used and its promise to the customers. The vendor (ArcSight) had managed to build a robust application framework which helped address an impressive variety of use cases. Powered by event, asset, and identity modeling, as well as robust content management capabilities, ArcSight SIEM was "killing it" in the security, compliance, and fraud monitoring spaces. The applications were limited only by the know-how and the imagination of the practitioner. Some of the advanced workflows we've built to help SOC analysts automate alert triage had been moderately sophisticated.
Content vs Code
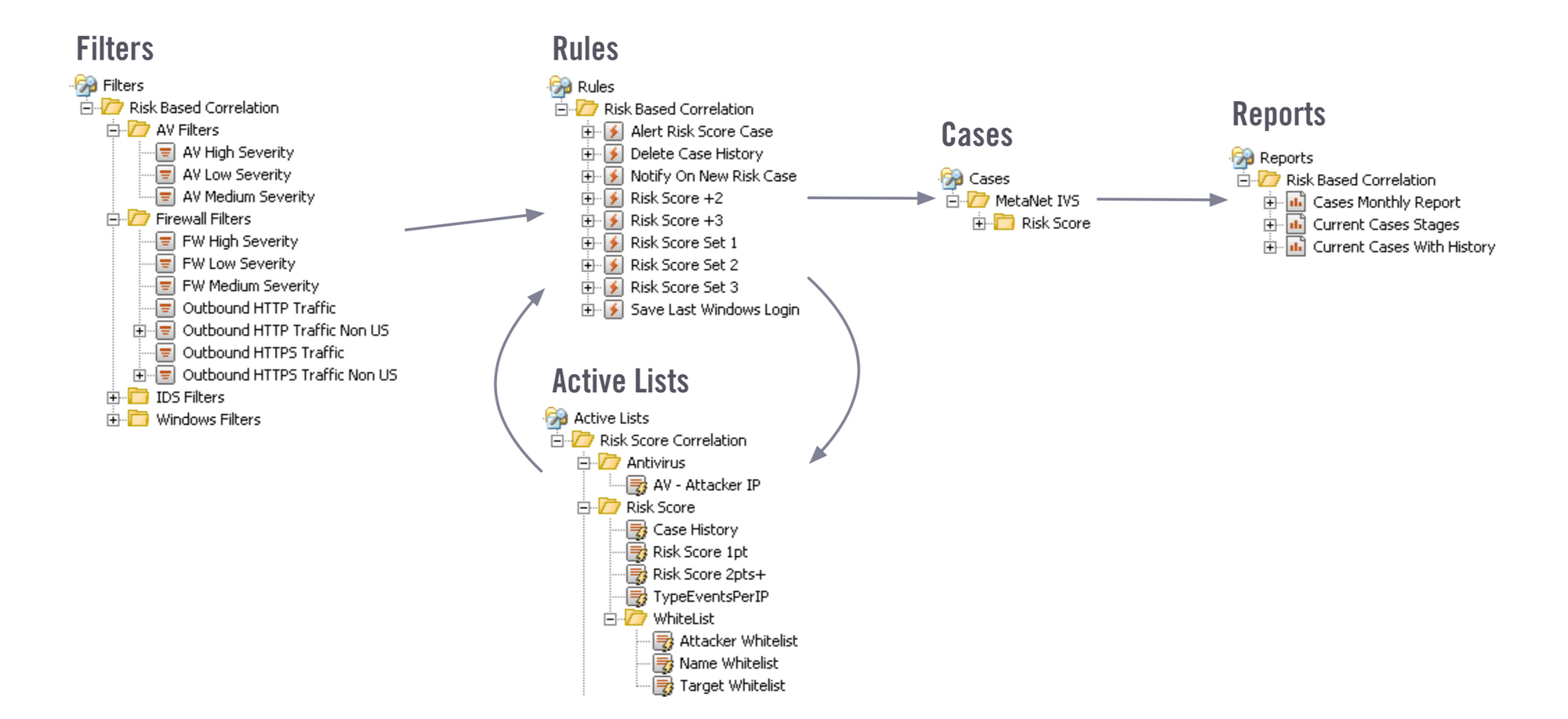
If the automation of manual tasks is the ultimate objective of cyber teams, content-driven frameworks are the ultimate way of delivering it. Code-based solutions simply don’t scale internally for customers. And while we may have been comfortable writing our own SQL based SIEM rules back in the day, it’s ridiculous in 2019.
Security analysts are looking to streamline detection, search, alert triage, incident analysis, and manage incident response. Being able to build a use case simply by interacting with the application, and without having to write python, SQL, or YAML is not just a good idea -- it’s a must-have. Enough has been said about the shortage of security skills. One of the reasons why we face this issue is the fact that too many of our tools rely on custom code and expensive one-off solutions, requiring specific technical skills and experience.
Automation for Everyone
Democratization is the ability to empower anyone to use your application. This simple concept seems to be lost on a lot of cybersecurity software vendors. I've spent the last 14 years building solutions which elevate user experience and break information down into friendly building blocks. Providing an ability to create use cases easily, and share and improve the content within a team or a community, is a must.
The framework must meet the needs of the most technically proficient user, and make complex use cases possible, while making it accessible and intuitive for any user, including teams outside of the cybersecurity organization. A big part of this is information modeling. If you’ve seen any of my presentations, you know what I’m talking about.
The practice of information security cannot exist in a vacuum. Its activities, deliverables, and information closely involve separate areаs of enterprise IT. Digital inventory management, compliance monitoring, assurance, provisioning, and many others. An automation framework must connect cybersecurity with the rest of the business, and must be accessible to all enterprise users.
To Action
We've stuck to these principles when building CRFT. Instead of competing on a quantity of half-baked features that pass the burden onto customer, we focus on accessibility, ease of use, and pure-play orchestration. You can think of CRFT as a glue that melds your information security automation needs with the rest of the IT, from alert triage and data enrichment to provisioning and compliance monitoring. Breezy on-boarding, code-less automation, a free subscription tier. Could this be the driver of positive change we're looking for? I hope so.
Let me know your thoughts.
